If you want to add the search box in your blogger.
Visit the site. Tips for New Bloggers: Add Blogger search box
Monday
Thursday
Guide to Split big file using Winrar
Step 1: Right click the File wou want to split. Then choose "Add to archive"
Step 2: Under General tab, there is an area that says "split to volume,bytes"
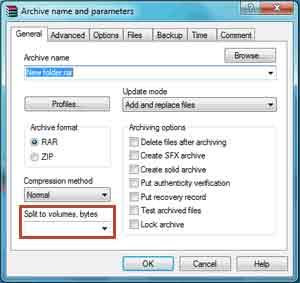
Step 3: Click down arrow, from the drop-down list,select the split.
Step 4: Type the size you want each part to be.
Step 5: Then click OK
After you finish all the steps above mentioned, it will split files into parts with the size you chose.
Download Winrar 3.9
Step 2: Under General tab, there is an area that says "split to volume,bytes"

Step 3: Click down arrow, from the drop-down list,select the split.
Step 4: Type the size you want each part to be.
Step 5: Then click OK
After you finish all the steps above mentioned, it will split files into parts with the size you chose.
Download Winrar 3.9
Wednesday
Good Morning
Too often we underestimate
The power of a touch, a smile,
a kind word, a listening ear,
an Honest Compliment,
or the smallest act of caring,
all of which have the potential
to turn a life around.
The power of a touch, a smile,
a kind word, a listening ear,
an Honest Compliment,
or the smallest act of caring,
all of which have the potential
to turn a life around.

What are you doing???
Let me seeeeeeeeeeeeeeeeeeeeee.........
OH MY GOD!!!!!!!!!!!!!!!!!!!!!!!!
Started working??
Anyway, I just disturbed you to wish you Good Morning JJ!!!!!!!!!
Have a nice day.
VNYRU4C2ZFSB
Funny
Born to be Software Enginner
One day ...
Teacher gave a punishment to me and asked me to write
"I Will Not Throw Paper Airplanes in the Class"
500 times on the black board.
and I wrote
 Coz I Born to be a Software Enginner.
Coz I Born to be a Software Enginner.
 Johny Johny
Johny Johny
Yes Papa
Private Company
Yes Papa
Any Motivation
No Papa
Many Tension
Yes Papa
Do u Sleep well
No Papa
Onsite Opportunity
No papa
Boss Ki Galiyan
Yes Papa
Increment
Ha ha ha :)
One day ...
Teacher gave a punishment to me and asked me to write
"I Will Not Throw Paper Airplanes in the Class"
500 times on the black board.
and I wrote
 Coz I Born to be a Software Enginner.
Coz I Born to be a Software Enginner.Johny-Johny Yes Papa
 Johny Johny
Johny JohnyYes Papa
Private Company
Yes Papa
Any Motivation
No Papa
Many Tension
Yes Papa
Do u Sleep well
No Papa
Onsite Opportunity
No papa
Boss Ki Galiyan
Yes Papa
Increment
Ha ha ha :)
Tuesday
Schedule a weekly defragmentation
If you think your computer has gotten slower since you bought it. One biggest factors that slows down your computer's performance is fragmentation,in which storage space is used inefficiently, reducing storage capacity and in most cases performance
Defragmenting your hard drive is the process of putting all the scattered pieces of files back together. Microsoft Windows XP includes a tool that will defragment your hard drive for you. To keep your system performing well, it’s a good idea to have Windows XP automatically defragment your hard drive every week.
To schedule a weekly defragmentation
1. Click Scheduled Task.
Start -> Accessories -> System Tool -> Scheduled Tasks

2. In the Scheduled Tasks window, double-click Add Scheduled Task.

3.In the Scheduled Task Wizard, Click Next.
 4. Click Browse.
4. Click Browse.
 5. In the File name box, type %systemroot%\system32\defrag.exe, and then click Open
5. In the File name box, type %systemroot%\system32\defrag.exe, and then click Open

 7. Set the time and day of the week you would like to defragment your hard drive. For best results, choose a time when your computer will be on but you will be away from it. Click Next.
7. Set the time and day of the week you would like to defragment your hard drive. For best results, choose a time when your computer will be on but you will be away from it. Click Next.
 8. Type your password in both the Enter the password and Confirm password boxes. Then, click Next.
8. Type your password in both the Enter the password and Confirm password boxes. Then, click Next.
 9. Select the Open advanced properties for this task when I click Finish check box, and then click Finish.
9. Select the Open advanced properties for this task when I click Finish check box, and then click Finish.

10. In the Run box, add C: to the existing command. Make sure you include a space before the “C:”. Then, click OK.
 11. In the Set Account Information dialog box, type your password in both the Password and Confirm password boxes. Then, click OK.
11. In the Set Account Information dialog box, type your password in both the Password and Confirm password boxes. Then, click OK.
 Windows XP will defragment your hard drive at the time you have scheduled. During defragmentation, a black window will open. If you happen to be working at your computer when the window opens, you can ignore it. The window will automatically disappear when defragmentation is complete.
Windows XP will defragment your hard drive at the time you have scheduled. During defragmentation, a black window will open. If you happen to be working at your computer when the window opens, you can ignore it. The window will automatically disappear when defragmentation is complete.
Monday
How To Password Protect Data on CDs or DVDs
Do you have Office documents, email messages, Photographs stored on a CD/DVD which you won't not like others to copy to a computer ?
The answer is simple. Encrypt and then password protect your CD or DVD.
All you need to password protect CDs or DVDs is True Crypt (or another software that can create encrypted containers). The Open Source encryption software can create so called containers that can be filled with data. These containers are password protected and can only be accessed if the correct password is supplied. The user does need True Crypt on the other hand to access the CDs and DVDs.Please note that this method is only working with data CDs or DVDs and not audio or video CDs or DVDs that shall be played in standalone players.
Start by downloading True Crypt from the official website. Click on the Create Volume button after installation. This opens a wizard that can be used to create an encrypted file container.
Step 1:
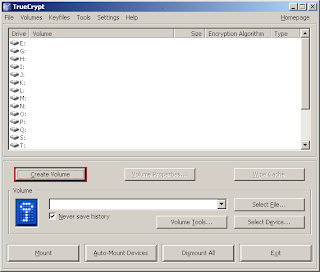 The main TrueCrypt window should appear. Click Create Volume (marked with a red rectangle for clarity).
The main TrueCrypt window should appear. Click Create Volume (marked with a red rectangle for clarity).
Step 2
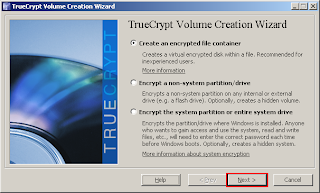 The TrueCrypt Volume Creation Wizard window should appear.
The TrueCrypt Volume Creation Wizard window should appear.
In this step you need to choose where you wish the TrueCrypt volume to be created. A TrueCrypt volume can reside in a file, which is also called container, in a partition or drive. In this tutorial, we will choose the first option and create a TrueCrypt volume within a file. As the option is selected by default, you can just click Next.
Note: In the following steps, the screenshots will show only the right-hand part of the Wizard window.
Step 3
The answer is simple. Encrypt and then password protect your CD or DVD.
All you need to password protect CDs or DVDs is True Crypt (or another software that can create encrypted containers). The Open Source encryption software can create so called containers that can be filled with data. These containers are password protected and can only be accessed if the correct password is supplied. The user does need True Crypt on the other hand to access the CDs and DVDs.Please note that this method is only working with data CDs or DVDs and not audio or video CDs or DVDs that shall be played in standalone players.
Start by downloading True Crypt from the official website. Click on the Create Volume button after installation. This opens a wizard that can be used to create an encrypted file container.
Step 1:
 The main TrueCrypt window should appear. Click Create Volume (marked with a red rectangle for clarity).
The main TrueCrypt window should appear. Click Create Volume (marked with a red rectangle for clarity).Step 2
 The TrueCrypt Volume Creation Wizard window should appear.
The TrueCrypt Volume Creation Wizard window should appear.In this step you need to choose where you wish the TrueCrypt volume to be created. A TrueCrypt volume can reside in a file, which is also called container, in a partition or drive. In this tutorial, we will choose the first option and create a TrueCrypt volume within a file. As the option is selected by default, you can just click Next.
Note: In the following steps, the screenshots will show only the right-hand part of the Wizard window.
In this step you need to choose whether to create a standard or hidden TrueCrypt volume. In this tutorial, we will choose the former option and create a standard TrueCrypt volume. As the option is selected by default, you can just click Next.
Step 4
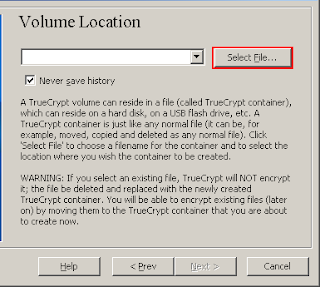

In this step you have to specify where you wish the TrueCrypt volume (file container) to be created. Note that a TrueCrypt container is just like any normal file. It can be, for example, moved or deleted as any normal file. It also needs a filename, which you will choose in the next step.
Click Select File.
The standard Windows file selector should appear (while the window of the TrueCrypt Volume Creation Wizard remains open in the background).
Click Select File.
The standard Windows file selector should appear (while the window of the TrueCrypt Volume Creation Wizard remains open in the background).
Step 5
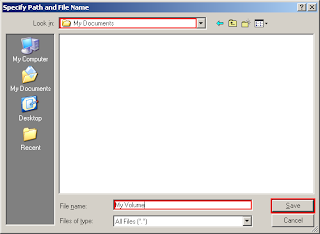
Click Save. The file selector window should disappear. In the following steps, we will return to the TrueCrypt Volume Creation Wizard.

In this tutorial, we will create our TrueCrypt volume in the folder D:\My Documents\ and the filename of the volume (container) will be My Volume (as can be seen in the screenshot above). You may, of course, choose any other filename and location you like (for example, on a USB memory stick). Note that the file My Volume does not exist yet – TrueCrypt will create it.
IMPORTANT: Note that TrueCrypt will not encrypt any existing files. If you select an existing file, it will be overwritten and replaced by the newly created volume (so the overwritten file will be lost, not encrypted). You will be able to encrypt existing files (later on) by moving them to the TrueCrypt volume that we are creating now.* Select the desired path (where you wish the container to be created) in the file selector. Type the desired container filename in the File name box.
IMPORTANT: Note that TrueCrypt will not encrypt any existing files. If you select an existing file, it will be overwritten and replaced by the newly created volume (so the overwritten file will be lost, not encrypted). You will be able to encrypt existing files (later on) by moving them to the TrueCrypt volume that we are creating now.* Select the desired path (where you wish the container to be created) in the file selector. Type the desired container filename in the File name box.
Click Save. The file selector window should disappear. In the following steps, we will return to the TrueCrypt Volume Creation Wizard.
Google SMS Service
You can now send SMS from your Gmail account directly to a mobile phone. Unfortunately, this service is available only for U.S. phones. SMS is actually a Gmail Labs feature and needs to be enabled before you can start using it.
Click on the Settings link (at the top right) and move to the Labs tab. You'll find "Text messaging (SMS) in Chat" way down the page so start scrolling. Select the Enable button and save the changes. Your Gmail account will load once again with the Labs feature now activated.
How do you send the SMS from Gmail
Click on the Settings link (at the top right) and move to the Labs tab. You'll find "Text messaging (SMS) in Chat" way down the page so start scrolling. Select the Enable button and save the changes. Your Gmail account will load once again with the Labs feature now activated.
How do you send the SMS from Gmail
Sending SMS from Gmail is really a simple process. Move the mouse cursor over a contact in the Chat window. Click on More (with a small blue downward arrow) and select Send SMS option. Now enter the mobile phone number. The small chat window is launched - you'll find it at the bottom right in which you type the SMS.
Please note, your contact may be charged for receiving the SMS so I suggest you don't go overboard.
SMS sent from Gmail chat will come from a 406 area code (US) number. The recipient can use this number to send a reply which gets routed back to Gmail servers to arrive at your chat window. Messages sent and received from different contacts will use different 406 numbers. However, messages from one contact will always use the same number. This means your contacts are assigned individual numbers and you can thus bookmark it in your phone.
Recipients can choose to stop receiving Gmail SMS by replying with the word BLOCK. And if you decide not to receive messages through Gmail from any of your friends, you can reply with STOP.
Please note, your contact may be charged for receiving the SMS so I suggest you don't go overboard.
SMS sent from Gmail chat will come from a 406 area code (US) number. The recipient can use this number to send a reply which gets routed back to Gmail servers to arrive at your chat window. Messages sent and received from different contacts will use different 406 numbers. However, messages from one contact will always use the same number. This means your contacts are assigned individual numbers and you can thus bookmark it in your phone.
Recipients can choose to stop receiving Gmail SMS by replying with the word BLOCK. And if you decide not to receive messages through Gmail from any of your friends, you can reply with STOP.
Track Your Lost Mobile Phone
Now a days each one of us carry Hi Fi Mobile devices and always fear that it may be stolen. But now you don't have to worry, you can easily track your mobile phone.
Each mobile carries a unique IMEI i.e International Mobile Identity Number. which can be used to track your mobile anywhere in the world.
Let me explain you how it works
1. Dial *#06# from your mobile.
2. Your mobile shows a unique 15 digit.
3. Note down this Number, as this number is very important which will
help trace your mobile in case of theft.
4. If your mobile got stolen you just have to mail this 15 digits IMEI Number
to cop@vsnl.net
5. Your Mobile will be traced within next 24 hrs via a complex system of GPRS
and Internet
Create small easy to read URL's
Create easy to read and type Internet addresses from long addresses often found on popular sites such as Amazon, eBay, MapQuest, etc. by using online services that shrink the address.
For example, the URL: http://techleren.blogspot.com/2009/11/snow-effect-in-blogger.html would become: http://snipurl.com/t5cl8. Below are examples of sites that allow you to copy and paste any URL into them to make them smaller.
For example, the URL: http://techleren.blogspot.com/2009/11/snow-effect-in-blogger.html would become: http://snipurl.com/t5cl8. Below are examples of sites that allow you to copy and paste any URL into them to make them smaller.
* http://tinyurl.com/
* http://snipurl.com/
* http://tubeurl.com/
* http://cuturl.com/
In addition to visiting one of the above sites each time you need to make a URL smaller if you're running Mozilla Firefox there are many tinyurl and other Firefox add-ons that allow you to integrate this feature into your browser.
Sunday
Snow Effect in Blogger
1. Log in to your Blogger Account.
2. Click Layout and go to page element.
3. Click Add Gadget, then click HTML/JavaScript.
4. Copy and paste the below code<script src="http://gujaratisite.com/blogger/snow.js" type="text/javascript">
</script>
5. After completing the above step Click Save.
JavaScript Tricks
Here i will list some of very cool JavaScripts hacks and tricks that can be used creatively or just to have fun. To make this codes work, all you have to do is copy and paste the above code into the address bar of your browser window and hit "Enter". So enjoy the code.
Edit Whatever you want on ANY Page
Edit Whatever you want on ANY Page
This code lets you edit any website page. With this code, you can edit and save the modified pages to your Computer.
Rotate Image on Web Page
Finding Spoof Websites
Sometimes we are Not sure whether the website that you are visiting is authentic. Use this code whenever in doubt
javascript:document.body.contentEditable='true'; document.designMode='on'; void 0 |
Rotate Image on Web Page
This code pull off all the images from your web page and rotates them in circle. You can test
this code on a websites with many images.
this code on a websites with many images.
javascript:R=0; x1=.1; y1=.05; x2=.25; y2=.24; x3=1.6; y3=.24; x4=300; y4=200; x5=300; y5=200; DI=document.getElementsByTagName("img"); DIL=DI.length; function A(){for(i=0; i-DIL; i++){DIS=DI[ i ].style; DIS.position='absolute'; DIS.left=(Math.sin(R*x1+i*x2+x3)*x4+x5)+"px"; DIS.top=(Math.cos(R*y1+i*y2+y3)*y4+y5)+"px"}R++}setInterval('A()',5); void(0); |
You can do little experiment by changing "img" tag. Just replace it with “a” or “p” and watch some links or text rotate instead of images.
Finding Spoof Websites
Sometimes we are Not sure whether the website that you are visiting is authentic. Use this code whenever in doubt
javascript:alert("The actual URL is:\t\t" + location.protocol + "//" + location.hostname + "/" + "\nThe address URL is:\t\t" + location.href + "\n" + "\nIf the server names do not match, this may be a spoof."); |
Friday
How to Enable Net Send Messenger Service on Windows XP
Sends messages to other users, computers, or messaging names on the network. If you installed Windows XP Service Pack2 or later, the Messenger service was disabled in order to prevent the net send spam that was getting popular a few year ago. You can manually re-enabled the Messenger service again to allow you to send and receive net messages.
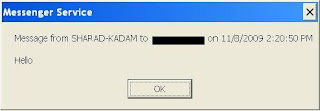
If service is not enabled then you will receive the error. In Order to enable the Service follow this steps. • Open Control Panel. • Open Administrative Tools • Open Component Service • Look for Service named “Messenger”. • Double click service.
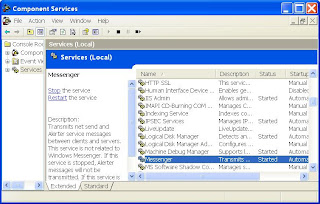
Choose “Automatic” for startup type. Then click the “Start” button to start the service.
Ask the friend you want to message to enable it too(Messenger service), then you will be able to send quick messages to your friend. If you are on same network, the computer name or Windows login name will work. Otherwise, the IP address will do the work.
The Syntax:
net send [computer name|login name|ip address] [message]

If service is not enabled then you will receive the error. In Order to enable the Service follow this steps. • Open Control Panel. • Open Administrative Tools • Open Component Service • Look for Service named “Messenger”. • Double click service.

Choose “Automatic” for startup type. Then click the “Start” button to start the service.
Ask the friend you want to message to enable it too(Messenger service), then you will be able to send quick messages to your friend. If you are on same network, the computer name or Windows login name will work. Otherwise, the IP address will do the work.
The Syntax:
net send [computer name|login name|ip address] [message]
Automatic Windows Shutdown with Scheduled Tasks
You can shutdown Window automatically without using any external software. Use the tools provided by windowss. Scheduled Tasks gives you an easy interface to scheduled an application to run at certain time. Shutdown.exe is a DOS command that can locally and remotely shut down your computer.
Let me give some detail about Shutdown.exe.
Usage: shutdown [-i | -l | -s | -r | -a] [-f] [-m \\computername]
[-t xx] [-c "comment"] [-d up:xx:yy]
No args Display this message (same as -?)
-i Display GUI interface, must be the first option
-l Log off (cannot be used with -m option)
-s Shutdown the computer
-r Shutdown and restart the computer
-a Abort a system shutdown
-m \\computername Remote computer to shutdown/restart/abort
-t xx Set timeout for shutdown to xx seconds
-c "comment" Shutdown comment (maximum of 127 characters)
-f Forces running applications to close without warning
-d [u][p]:xx:yy The reason code for the shutdown
u is the user code
p is a planned shutdown code
xx is the major reason code (positive integer less than 256)
yy is the minor reason code (positive integer less than 65536)
Next Open Windows Scheduled Tasks by going to
Start -> Accessories -> System Tools -> Scheduled Tasks
 Now double click on “Add Scheduled task” and click “Browse” to look for shutdown.exe
Now double click on “Add Scheduled task” and click “Browse” to look for shutdown.exe
Browse for shutdown.exe located in C:\WINDOWS\System32\shutdown.exe. This exe is used to shutdown our computer. Give the task any name you want, for e.g., “Auto Shutdown” and make sure to check Perform task option button. You can select any option depending on your requirement. I selected “One time only”.

Keep clicking Next as the dialogue are self explanatory, being sure to provide your windows password when needed until the last prompt. Finally after completing the above step you need to customize the shutdown command slightly further so check “Open advanced properties” before you click Finish.

As the advanced dialogue opens, add “-s -f” to the end of the command as shown in the red box. The “-s” option specifies a shutdown and the “-f” command forces all application to close.

When everything is done, you can see a new scheduled task, You can now take the rest, system will automatically shutdown.

Write Batch File to Start Program in Startup
You can start your computer applications automatically and control the sequence of the programs when your computer comes up. Here we consider you want to run three different applications (WordPad, calculator, and notepad) and minimized automatically with sequence at windows startup. However, you can write a batch file to do the job for you. Open any text editor like notepad and type the following command.
 Now choose the option, Save As to save this file with .bat extension. For example filename.bat. Enclosed the name in double quote at the time save like “Mystartup.bat”
Now choose the option, Save As to save this file with .bat extension. For example filename.bat. Enclosed the name in double quote at the time save like “Mystartup.bat”
Now Right- click on Start button and choose open > Double click Programs > here open Startup folder. Now drag your .bat file in the Startup folder and close the dialog box.
Next time When you restart the computer, WordPad, Calc will start first and then Notepad. You won't see the batch file run because you told it to run minimized.
 Now choose the option, Save As to save this file with .bat extension. For example filename.bat. Enclosed the name in double quote at the time save like “Mystartup.bat”
Now choose the option, Save As to save this file with .bat extension. For example filename.bat. Enclosed the name in double quote at the time save like “Mystartup.bat”Now Right- click on Start button and choose open > Double click Programs > here open Startup folder. Now drag your .bat file in the Startup folder and close the dialog box.
Next time When you restart the computer, WordPad, Calc will start first and then Notepad. You won't see the batch file run because you told it to run minimized.
Remove Virus from USB
One of the ways by which a virus can infect your PC is through USB/Pen drives. Common viruses such as ’Ravmon’ , ‘New Folder.exe’, ‘Orkut is banned’ etc are spreading through USB drives. Most anti virus programs are unable to detect them and even if they do, in most cases they are unable to delete the file, only quarantine it. Here are the things which you can do if you want to remove such viruses from your USB Drive Whenever you plug a USB drive in your system, a window will appear similar to the one shown below
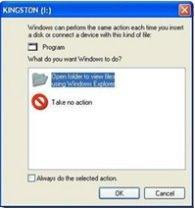
Don’t click on Ok , just choose ‘Cancel’. Open the Command Prompt by typing ‘cmd‘ in the run box.
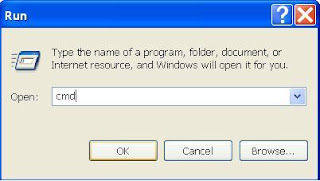
In the command prompt type the drive letter: and press enter . Now type dir /w/a and press enter.
This will display a list of the files in the pen drive. Check whether the following files are there or not
* Autorun.inf
* Ravmon.exe
* NewFolder.exe
* svchost.exe
* Heap41a
* or any other exe file which may be suspicious.
If any of the above files are there, then probably the USB drive is infected. In command prompt type attrib -r -a -s -h *.* and press enter. This will remove the Read Only, Archive, System and hidden file attribute from all the files. Now just delete the files using the command del filename. e.g Del Ravmon.exe
example del Ravmon.exe. Delete all the files that are suspicious. To be on a safer side, just scan the USB drive with an anti virus program to check whether it is free of virus or not. Now remove the drive and plug it again. In most of the cases, the real culprit turns out to be the “Autorun.inf” file which mostly gets executed when someone clicks Ok in the dialog window which appears above. Thus the infections can spread
Security Tip:
Disable the Autoplay feature of USB drives. If you disable the Autoplay feature of USB drives, then there are lesser chances of the virus spreading.

Don’t click on Ok , just choose ‘Cancel’. Open the Command Prompt by typing ‘cmd‘ in the run box.

In the command prompt type the drive letter: and press enter . Now type dir /w/a and press enter.
This will display a list of the files in the pen drive. Check whether the following files are there or not
* Autorun.inf
* Ravmon.exe
* NewFolder.exe
* svchost.exe
* Heap41a
* or any other exe file which may be suspicious.
If any of the above files are there, then probably the USB drive is infected. In command prompt type attrib -r -a -s -h *.* and press enter. This will remove the Read Only, Archive, System and hidden file attribute from all the files. Now just delete the files using the command del filename. e.g Del Ravmon.exe
example del Ravmon.exe. Delete all the files that are suspicious. To be on a safer side, just scan the USB drive with an anti virus program to check whether it is free of virus or not. Now remove the drive and plug it again. In most of the cases, the real culprit turns out to be the “Autorun.inf” file which mostly gets executed when someone clicks Ok in the dialog window which appears above. Thus the infections can spread
Security Tip:
Disable the Autoplay feature of USB drives. If you disable the Autoplay feature of USB drives, then there are lesser chances of the virus spreading.
Wednesday
How to find the IP address of the email sender
When you receive an email, you receive more than just the message. The email comes with headers that carry important information that can tell where the email was sent from and possibly who sent it. For that, you would need to find the IP address of the sender. The tutorial below can help you find the IP address of the sender.
If you receive an email sent from a Gmail account through the web browser, you may not be able to find the real IP address because Google hides the real IP address of the sender. However, if someone sends you a mail from his/her Gmail account using a client like Thunderbird, Outlook or Apple Mail, you can find the originating IP address.
Finding IP address in Gmail
- Log into your Gmail account.
- Open the mail. For which you want to trace the address.
- To display the email headers, Click on the inverted triangle beside Reply. Select Show Original
- Copy Header displayed in above step and use IP address detection script to ease the process. You can use Free Tool
- Look for Received: from followed by the IP address between square brackets [] Received: from mx008.twitter.com (mx008.twitter.com [128.121.146.144])
- If you find more than one Received: from patterns, select the last one.
- Finally track the IP address of the sender

Finding IP Address in Yahoo! Mail
- Log into your Yahoo mail account.
- Open the mail for which you want to trace address.
- Click the subject of mail you want to trace and right click.
- Copy the header displayed in above step and use the IP Detection Tool.
- Look for Received: from followed by the IP address between square brackets []
- Trace the IP address of the sender.
Privacy Policy
Privacy Policy for techleren.blogspot.com
If you require any more information or have any questions about our privacy policy, please feel free to contact us by email at sharad.kadam775@gmail.com.
At techleren.blogspot.com/, the privacy of our visitors is of extreme importance to us. This privacy policy document outlines the types of personal information is received and collected by techleren.blogspot.com/ and how it is used.
Log Files
Like many other Web sites, techleren.blogspot.com/ makes use of log files. The information inside the log files includes internet protocol ( IP ) addresses, type of browser, Internet Service Provider ( ISP ), date/time stamp, referring/exit pages, and number of clicks to analyze trends, administer the site, track user’s movement around the site, and gather demographic information. IP addresses, and other such information are not linked to any information that is personally identifiable.
Cookies and Web Beacons
techleren.blogspot.com/ does use cookies to store information about visitors preferences, record user-specific information on which pages the user access or visit, customize Web page content based on visitors browser type or other information that the visitor sends via their browser.
If you require any more information or have any questions about our privacy policy, please feel free to contact us by email at sharad.kadam775@gmail.com.
At techleren.blogspot.com/, the privacy of our visitors is of extreme importance to us. This privacy policy document outlines the types of personal information is received and collected by techleren.blogspot.com/ and how it is used.
Log Files
Like many other Web sites, techleren.blogspot.com/ makes use of log files. The information inside the log files includes internet protocol ( IP ) addresses, type of browser, Internet Service Provider ( ISP ), date/time stamp, referring/exit pages, and number of clicks to analyze trends, administer the site, track user’s movement around the site, and gather demographic information. IP addresses, and other such information are not linked to any information that is personally identifiable.
Cookies and Web Beacons
techleren.blogspot.com/ does use cookies to store information about visitors preferences, record user-specific information on which pages the user access or visit, customize Web page content based on visitors browser type or other information that the visitor sends via their browser.
Tuesday
Print labels for CDs and DVDs
Printing labels, whether they are for a DVD or a CD, with an inkjet printer is fairly simple, you do not required any additional software it is already is installed on your computer. The great thing about modern computing is that everyone in the industry assumes that people are creating media in their homes, so you have a lot of options.
Follow the steps:
3. Put the blank DVD labels into the inkjet printer’s paper feed. And Print the label.
4. Carefully peel the new label off of the backing and apply it to the DVD.
5. Firmly press the label to the DVD. Examine it to be certain that you have lined it up properly. If it is not lined up and paper hangs over the edge, you could damage your DVD player.
Follow the steps:
1. Acquire the physical labels. You can find printable labels in any store selling printer paper. A number of companies manufacture and distribute blank DVD and CD labels that are designed to be used with an inkjet printer. You will also need publishing software to design and print your labels.
2. Design your label with the publishing software.3. Put the blank DVD labels into the inkjet printer’s paper feed. And Print the label.
4. Carefully peel the new label off of the backing and apply it to the DVD.
5. Firmly press the label to the DVD. Examine it to be certain that you have lined it up properly. If it is not lined up and paper hangs over the edge, you could damage your DVD player.
Google Voice Search for your Phone

Good news for mobile users. The user who carry Nokia N-Series or E-Series, Android, Blackberry and iPhone mobile phone. You can now download the Google Mobile app for your Mobile phone and search Google using simple voice commands.
This application kept the browse history. Quickly search again for queries you recently performed.
Image Optimization
There is always a struggle between quality of the photo placed on the website and its size. Being of high quality the picture also appears to be of big file size and thus requires a lot of time to load, which in its turn causes problems with site viewing. This is where image optimization come to resolve such kind of problems.
Actually, you can do some optimization on your images to make it more suitable for the web presentation. The idea is to reduce the size of your graphics so that they take as few bytes as possible while retaining acceptable quality or make it as visually indifferent.
Let me show you how we can do it:
1. Resize image to the size required. Uploading 2000 x 1000px image and showing it at 600 x 400 px in your html page is of no meaning. You may resize image, or edit picture or even crop photos. Never use images directly from your camera.
2. Upload all images to ImageShack Imageshack – it makes your job faster by providing multiple image uploading feature. Upload all images and get direct url of images. you can use this URL to display the image in your site.
3. you can use some graphical tools to save image into different quality or compression level. You can use Image Optimizer this tool.
It’s really simple to use. Just provide your image url or upload your image and click the “Optimize” button. The website will then process your image and provide you a list of optimized images to choose. You can then save the image to use it.
Recommended: Don’t use GIF format on websites unless the image you use is an animated one. Use PNG as alternative of GIF as they too support transparent backgrounds and occupy less space.
Actually, you can do some optimization on your images to make it more suitable for the web presentation. The idea is to reduce the size of your graphics so that they take as few bytes as possible while retaining acceptable quality or make it as visually indifferent.
Let me show you how we can do it:
1. Resize image to the size required. Uploading 2000 x 1000px image and showing it at 600 x 400 px in your html page is of no meaning. You may resize image, or edit picture or even crop photos. Never use images directly from your camera.
2. Upload all images to ImageShack Imageshack – it makes your job faster by providing multiple image uploading feature. Upload all images and get direct url of images. you can use this URL to display the image in your site.
3. you can use some graphical tools to save image into different quality or compression level. You can use Image Optimizer this tool.
It’s really simple to use. Just provide your image url or upload your image and click the “Optimize” button. The website will then process your image and provide you a list of optimized images to choose. You can then save the image to use it.
Recommended: Don’t use GIF format on websites unless the image you use is an animated one. Use PNG as alternative of GIF as they too support transparent backgrounds and occupy less space.
Subscribe to:
Posts (Atom)


